Splunk Field Search: Splunk Tutorial
In this tutorial, we are going to learn about the splunk field search feature along with how to choose from fields and find out about their summaries as well.
Splunk Field Search
Previously, we have learned about how to do basic searching in Splunk, now we are going to do extensive field search on our titanic.csv file. Let’s look at the right sidebar where field sets are present and click on ‘All Fields’. It will open up all the current fields present inside the dataset.
Selecting Fields
We have the freedom to select and unselect fields when we see a list of all fields in front of us. If you select the option of ‘Select All within Filter’; then all fields will be selected. Similarly, if you want to unselect all fields you can select the ‘Deselect All’ option.
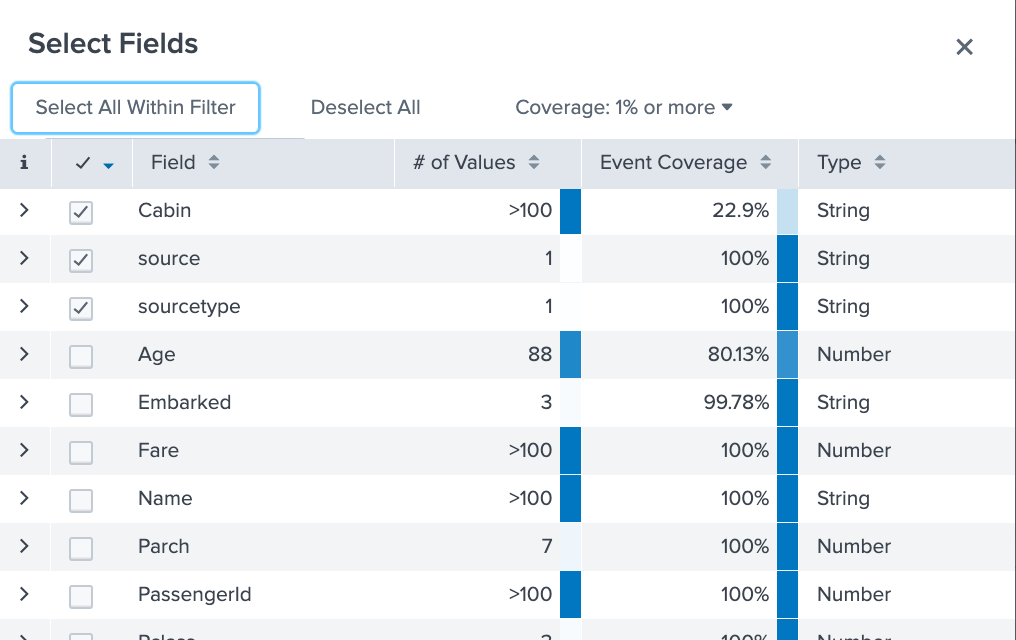
If you carefully notice, there is a field search table as well that has different columns related to the unique values, data type, event percentage present in those fields.
Summary of Fields
After selecting certain or all fields, you can view the summary of each field by simply clicking on the specific field. Once you do it, then you will see an option of ‘Select again with a toggle of Yes or No, if you want to see the specific field as your selected field then do not change anything. Let’s say if you select ‘Age’ from your field search which is a numeric value then you are gonna see Average, Min and Max and Standard Deviation already calculated belonging to that field.

This field summary will also show the ‘Top 10’ values that are recurring and that occupies the highest percentage of values (repeated) along with its count.
Using Field Search
Let’s search one of the fields now and add a certain condition to it. Let’s say we want to find the ‘Fare’ of the passenger tickets whose age has been 26 years so we will use a query to search:
Age="26" AND Fare="*"

Above you can that the result is only showing Fares of people whose age is 28, there are about 18 total entries.



