Splunk Source Types: Splunk Tutorial
In this tutorial, we are going to learn about how to perform splunk basic search along with using some search terms and using AND/OR built in operators to classify our research.
Splunk Basic Searching
Splunk has an excellent feature that empowers us to search through the whole dataset that we have just imported using the ingestion method. We can access this functionality on the main menu interface (left side) on the ‘Search & Reporting app’ section once you log into Splunk dashboard.
Once we click on search and Reporting app button, then we will redirected to a page with a search box where we can start searching on our data that we have just uploaded through the data ingestion process.
Using Search Terms
Let’s find the host in our current dataset by typing the name of our computer as our host by typing host=”Hiras-MacBook-Air.local” and then clicking the on the search icon on the right corner. Here, you will see that the searched term is highlighted.
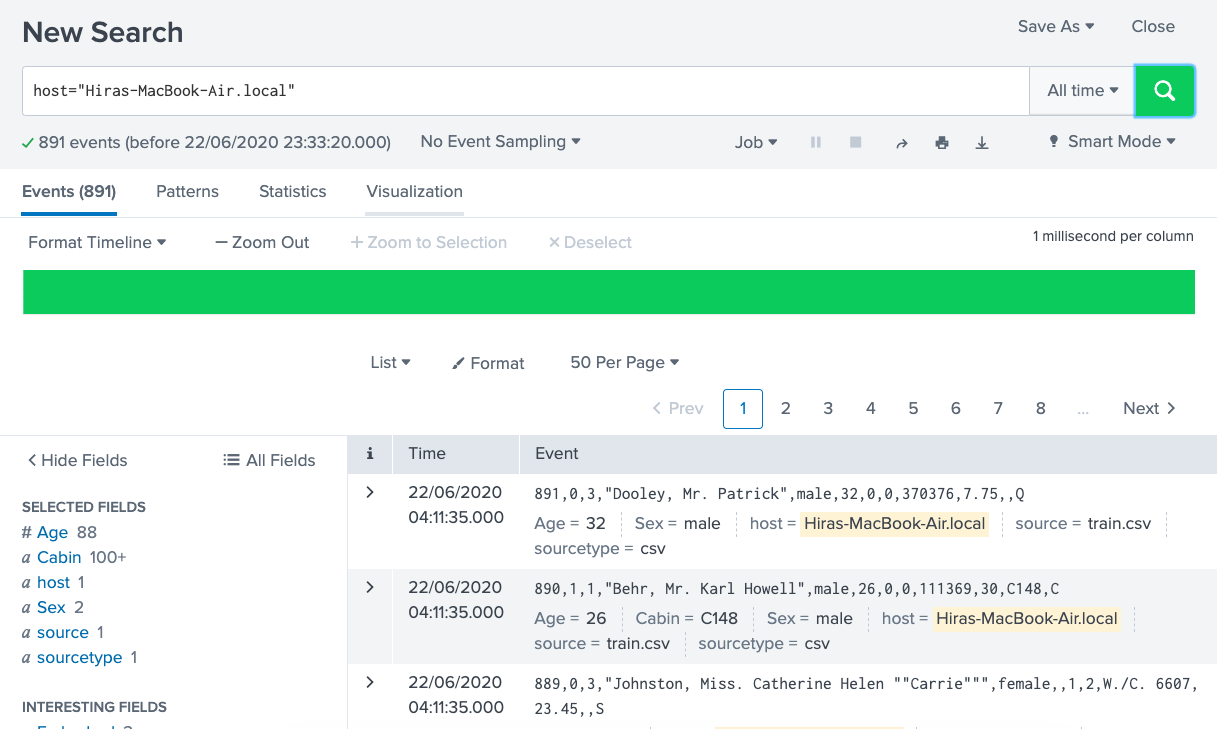
Remember to put double quotes around the terms that you are searching for and then join it with the search fields like host, source or source type etc. You can search more than one search fields.
Let’s say we want the sampling of the events to highlight the Cabin B24, we can do that by entering:
Cabin=”B42″
It will return us the following result:

Using AND/OR Operators For Research
We can use AND/OR operators inside our search option as well. Let’s say we want to find the age 26 of people that were boarded on titanic and we want their respective Gender/Sex to list as well, so we will be using the following syntax: Age=”26″ AND Sex=”female”. We will only get values where age is 26 and sex is female.

Above, you can see that we have 5 events that means there were 5 females of age 26 present inside titanic according to the sampling that we performed, you can test other search fields too to check your own data/event sampling so that the data makes more sense.



